A very common attack technique in use today is the Denial of Service (DoS) attack. DoS attacks are effective in degrading the performance of targeted systems, effectively taking them offline and preventing legitimate system use. A typical DoS attack goes like this:
- The attacker identifies one or more computers on the Internet as targets
- The attacker determines what ports the targets service for legitimate services e.g. port 80 for web servers, port 25 for SMTP
- The attacker sends a flood of network traffic to the target server and port
- The target must process all of the traffic to service the real requests
- The target cannot maintain desired performance levels while continuing to process the massively increased traffic
- The target either shuts down entirely or begins to service less than 100% of the requests
The degradation of performance, whether it is a shutdown or a reduction or delay in traffic processing, marks the success of a Denial of Service attack. If the attack is unsuccessful when conducted from a single host it can be scaled out to multiple attacking hosts. This results in a Distributed Denial of Service (DDoS) attack which is exceptionally difficult to defend against.
Most IT professionals want to know whether their systems can withstand a DoS attack. Luckily there is a great tool available to test this scenario. And it is the same tool that attackers frequently use to conduct actual attacks. It is the Low Orbit Ion Cannon.
Using the Low Orbit Ion Cannon
I often recommend to system administrators to use actual attacker tools to determine the security and resilience of a connected system. The Low Orbit Ion Cannon (LOIC) is a great and simple tool for DoS and DDoS testing.
The Low Orbit Ion Cannon can be downloaded from Sourceforge in a few forms. I’ll demonstrate it here using the Java version as shown in Figure 1.
Figure 1. The default Low Orbit Ion Cannon startup screen.
To test a server, simply type in the IP address in the Host field or the FQDN in the URL field. I’m going to use 10.0.1.1 here, a server on my network. Once I press Get it locks the IP address in as the target as shown in Figure 2.
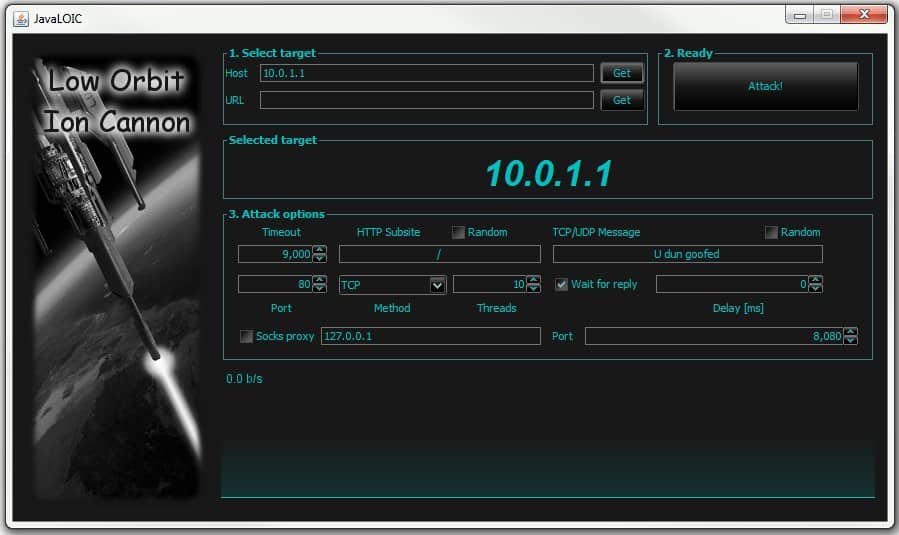
Figure 2. Targeting 10.0.1.1 with the Low Orbit Ion Cannon.
Next I select a port and protocol that I believe the target will process. Since this server handles HTTP requests I’ll target port 80. Now all I do is click Attack! and the Low Orbit Ion Cannon starts to fire network traffic at the server as shown in Figure 3.
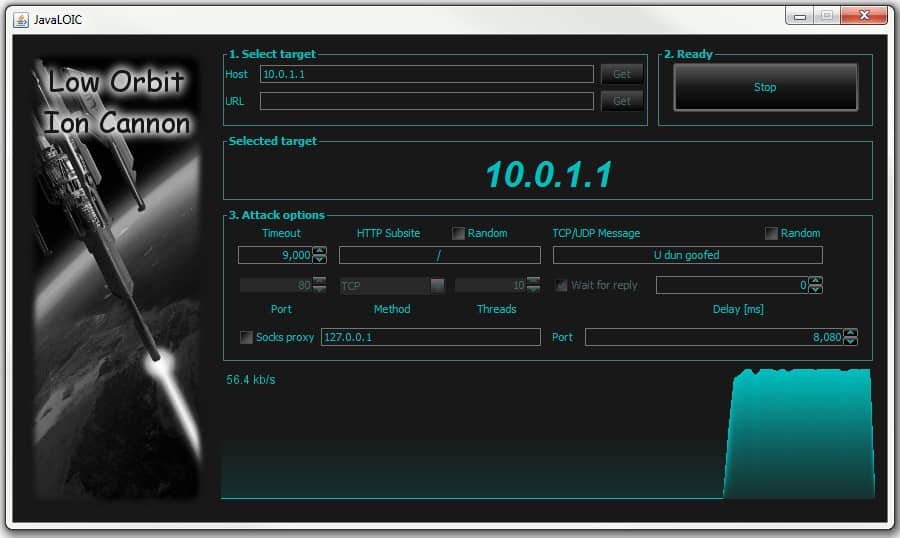
Figure 3. An attack in progress!
This attack is using the default values for network timeout, threads, traffic, and delay. And even though the default traffic volume appears to be relatively low, this attack is consuming roughly 20% of the CPU resource on the target server. The target server is not protected from DoS in any special way but does have both a host-based and network-based firewall. So one attacker, through a switch and two firewalls, can consume 20% CPU utilization.
What Do I Do With This Test?
Once you’ve conducted the test on your own non-production systems you will have a fairly clear idea of the potential impact that this type of attack will have. From there you need to determine whether countermeasures are required or justified based on a Return on Investment (ROI) calculation. The test simulates an attack and leaves the remediation options to you.
So now you know how a DoS attack works and how it will impact your systems. And knowing is half the battle!
Stay safe!
enoK -CISSP / MCSE / PMP